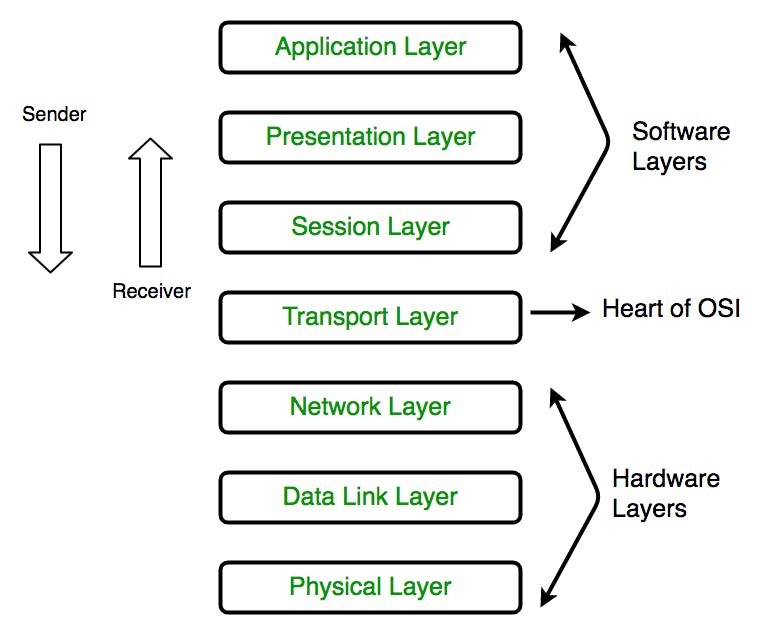
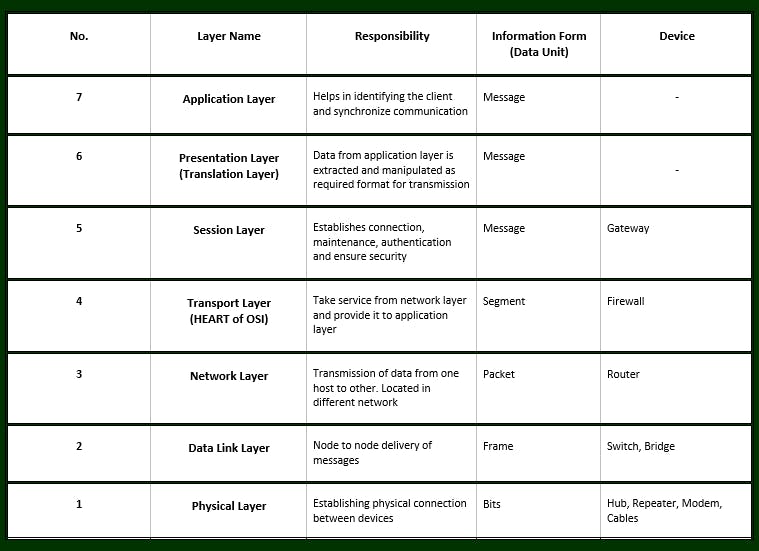
Layers of OSI Model
OSI stands for 'Open Systems Interconnection'. It has been developed by ISO – ‘International Organization for Standardization’ in the year 1984. It is a 7 layer architecture with each layer having specific functionality to perform. All these 7 layers work collaboratively to transmit the data from one person to another across the globe.
Application Layer
The interaction with the user or the user application takes place at this stage.
It is responsible for the actual physical connection between the devices. The physical layer contains information in the form of bits.
It consists of Client-server Architecture and Peers to Peer Architecture.
Example: Application – Browsers, Skype Messenger, etc.
Presentation Layer
- The presentation layer is also called the Translation layer
- The data from the application layer is extracted here and manipulated as per the required format to transmit over the network.
- The functions of the presentation layer are : Translation: For example, ASCII to EBCDIC. Encryption/ Decryption: Data encryption translates the data into another form or code. The encrypted data is known as the ciphertext and the decrypted data is known as plain text. A key value is used for encrypting as well as decrypting data. Compression:* Reduces the number of bits that need to be transmitted on the network.
Session Layer
This layer is responsible for the establishment of connection, maintenance of sessions, and also ensures security.
Authentication and authorization happen at this layer.
This layer can also terminate or end any session or transmission which is complete.
For Example : Let us consider a scenario where a user wants to send a message through some Messenger application running in his browser. The “Messenger” here acts as the application layer which provides the user with an interface to create the data. This message or so-called Data is compressed, encrypted (if any secure data), and converted into bits (0’s and 1’s) so that it can be transmitted.

Transport layer
- The transport layer provides services to the application layer and takes services from the network layer. The data in the transport layer is referred to as Segments
It is responsible for the End to End Delivery of the complete message.
It takes information from Network layer and sends it to Application layer.
- Transport Layer also takes care of Congestion control .
Network Layer
It acts as a network controller .
It transport Data from Sender’s Computer to Receiver’s Computer.
The sender & receiver’s IP addresses are placed in the header by the network layer.
Data-Link Layer
The data link layer is responsible for the node-to-node delivery of the message. The main function of this layer is to make sure data transfer is error-free from one node to another, over the physical layer.
Access to get the data is achieved at this layer.
Physical Layer
- Establishing Physical connections between devices.
OSI Model in a nutshell
TCP/IP Model [5 layers]
It stands for Transmission Control Protocol/Internet Protocol. The TCP/IP model is a concise version of the OSI model. It contains four layers, unlike seven layers in the OSI model. The layers are:
- Process/Application Layer
- Host-to-Host/Transport Layer
- Network Layer
- Network Access/Data-Link Layer
1. Application Layer
It is responsible for node-to-node communication and controls user-interface specifications. Some of the protocols present in this layer are HTTP, HTTPS, FTP, TFTP, Telnet, SSH, SMTP, SNMP, NTP, DNS, DHCP, NFS, X Window, LPD,POP3,VNC etc
Client-server Architecture
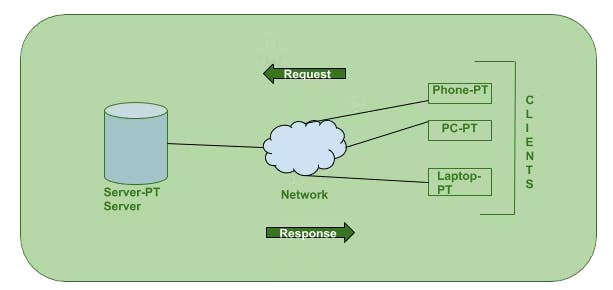
- In Client-server Architecture of a computer network in which many clients (remote processors) request and receive service from a centralized server (host computer).
- Client computers provide an interface to allow a computer user to request services of the server and to display the results the server returns.
- A collection server is known as a Datacenter.
- Datacenter is a collection of a huge number of computers. It may have static IP addresses. They have a good internet connection and high upload speed.
Peer-to-peer Architecture

- Peer-to-peer(P2P) computing or networking is a distrributed application architecture that partitions tasks or workloads between peers. Peers are equally privileged, equipotent participants in the application. They are said to form a peer-to-peer network of nodes.
- Every single computer can be named as a client as well as a server.
- It is a kind of decentralized network.
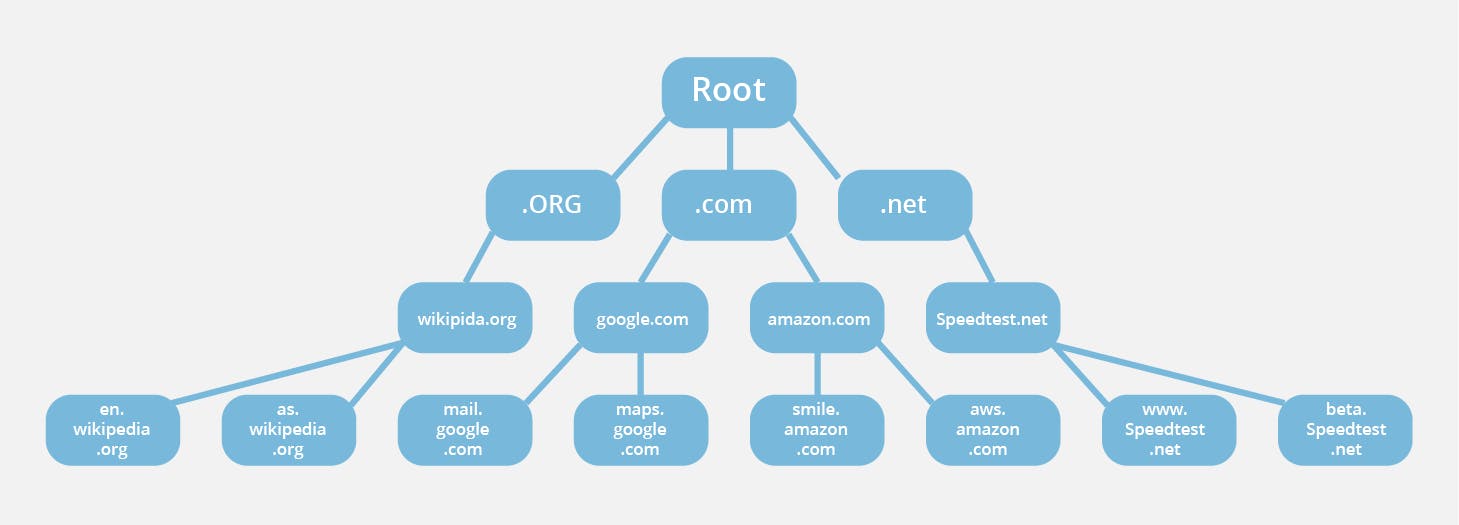
DNS-Domain Name System
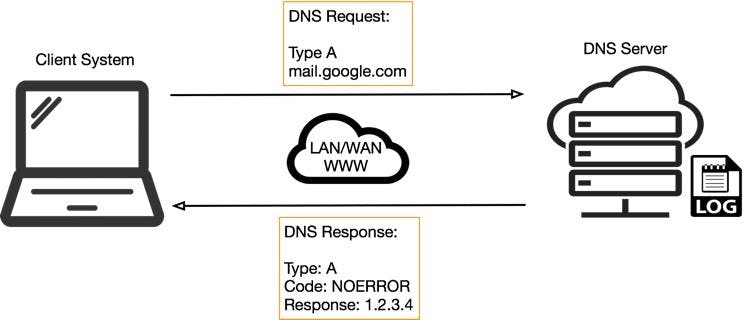
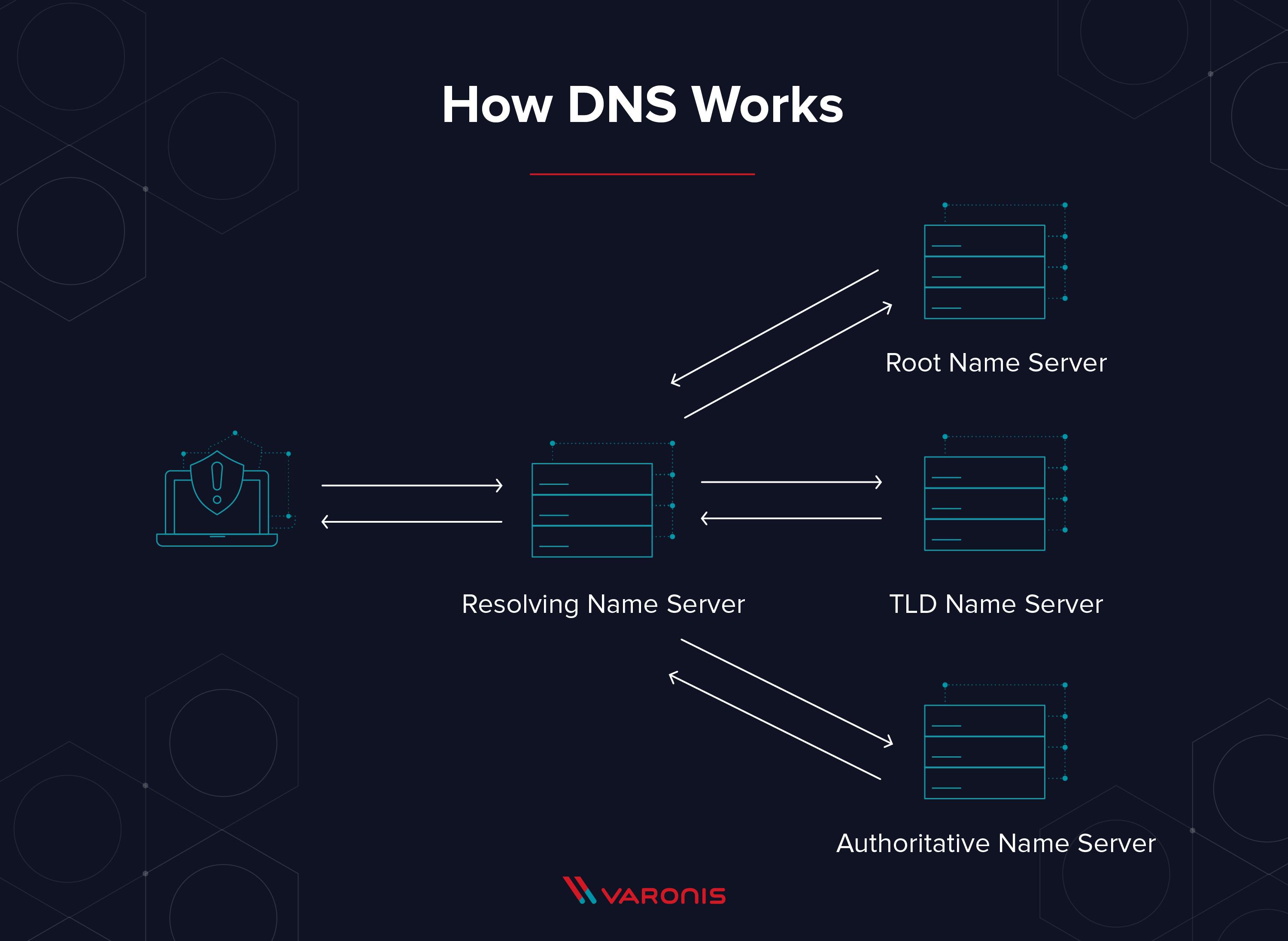
DNS is a hostname and mapped for IP address translation service. DNS translates domain names to IP addresses so browsers can load Internet resources.DNS servers eliminate the need for humans to memorize IP addresses such as 192.168.1.1 (in IPv4), or more complex newer alphanumeric IP addresses such as 2400:cb00:2048:1::c629:d7a2 (in IPv6).It is an application layer protocol for message exchange between clients and servers. For example: When we type "google.com ", HTTP protocol takes that domain name and uses DNS to find the IP address and afterward, it connects to that server.
-Root DNS Server
Root servers are DNS nameservers that operate in the root zone. These servers can directly answer queries for records stored or cached within the root zone, and they can also refer other requests to the appropriate Top Level Domain (TLD) server. The TLD servers are the DNS server group one step below root servers in the DNS hierarchy, and they are an integral part of resolving DNS queries.
2.Transport Layer
Transport Layer is the second layer in the TCP/IP model and the fourth layer in the OSI model. It is termed an end-to-end layer because it provides a point-to-point connection rather than a hop-to-hop (Network Layer), between the source host and destination host to deliver the services reliably.
- The transport layer attaches the socket port numbers to the segments.
- Some of the protocols present in this layer are TCP, UDP, SCTP, DCCP, ATP, FCP, RDP, RUDP, SST, SPX.
Objective of Transport layer.
- Flow control
- Congestion Control
- Multiplexing and Demultiplexing
- Process to process delivery
- End-to-end Connection between hosts
- Data integrity and Error correction
Transport layer Protocols
User Datagram Protocols (UDP)
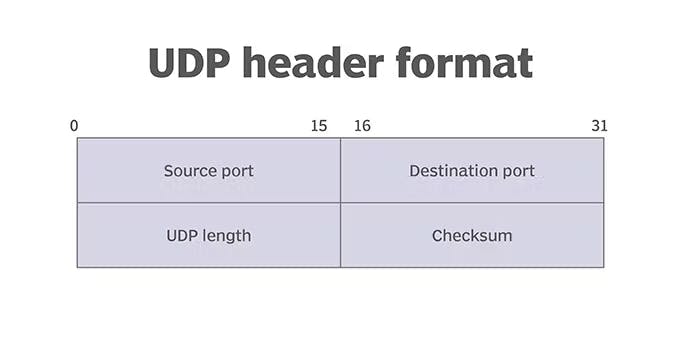
User Datagram Protocol (UDP) is a communications protocol that is primarily used to establish low-latency and loss-tolerating connections between applications on the internet. UDP speeds up transmissions by enabling the transfer of data before an agreement is provided by the receiving party.
UDP Header Composition
The User Datagram Protocol header has four fields, each of which is 2 bytes. They are the following:
- source port number
- destination port number
- length
- checksum
Applications of UDP
- Lossless data transmission
- Gaming, voice, and video
- Multicasting and routing update protocols
- Services that don't need fixed packet transmission
- Fast applications
Transmission Control Protocols(TCP)
TCP (Transmission Control Protocol) is one of the main protocols of the Internet protocol suite. It lies between the Application and Network Layers which are used in providing reliable delivery services. It is a connection-oriented protocol for communications that helps in the exchange of messages between the different devices over a network.
Features of TCP
- Segment Numbering System
- Flow Control
- Error Control
- Congestion Control
- Full Duplex (Bi-directional)
3. Network Layer
Network Layer is the third layer in the TCP/IP model and the fifth layer in the OSI model. It acts as a network controller. Its main function is to transfer network packets from the source to the destination. It is involved both the source host and the destination host. It provides a hop-to-hop connection, between the source host and the destination host to deliver the services reliably. The unit of data encapsulation is a segment.
Objectives of a Network Layer
- Flow control
- Congestion Control
- Error Control
Network Layer Protocol
Internet Protocol(IP)
Internet Protocols are a set of rules that governs the communication and exchange of data over the internet. Both the sender and receiver should follow the same protocols in order to communicate the data.
- It is a connectionless and unreliable protocol and to make it reliable and to make it reliable, it must be paired with a reliable protocol such as TCP at the transport layer.
- Internet protocol transmits the data in form of a datagram.
Control Plane
The control plane is the part of a network that controls how data packets are forwarded - meaning how data is sent from one place to another also can be referred to as the process of creating a routing table.
- Routers are referred to as Nodes.
- Link between routers is referred to as Edges.
Subnet Masking
- Subnet masking is going to mask the network port of the IP address and leaves us to the host part.
- You can set your subnet length.
- 20.0.0.0./35 - This means the first 35 bits are your subnet part.
Network Address Translation (NAT)
It is a method of mapping an IP address space into another by modifying network address information in the IP header of packets while they are in transit across a traffic routing device. NAT generally operates on a router or firewall.
4. Data-Link Layer
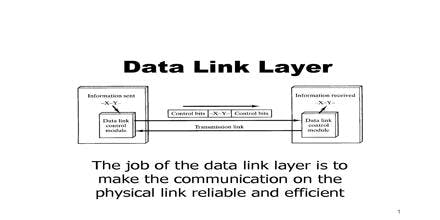
The Data-link layer is the second layer from the bottom in the OSI (Open System Interconnection) network architecture model. It is responsible for the node-to-node delivery of data. Its major role is to ensure error-free transmission of information. DLL is also responsible to encode, decode and organize the outgoing and incoming data. Some of the protocols present in this layer are SDLC, HDLC, SLIP, PPA, LAP, LCP, and NCP.
Sub-Layer of Data Link Layer:
- Logical Link Control(LLC)-This sublayer of the data link layer deals with multiplexing, the flow of data among applications and other services, and LLC is responsible for providing error messages and acknowledgments as well.
- Media Access Control(MAC)- MAC sublayer manages the device’s interaction, responsible for addressing frames, and also controls physical media access. The data link layer receives the information in the form of packets from the Network layer, it divides packets into frames and sends those frames bit-by-bit to the underlying physical layer.
Functions Of the Data-Link Layer:
- Framing
- Addressing
- Error Control
- Flow Control
Inspired by Kunal Kushwaha Devops Bootcamp Tutorial and Saiyam Pathak for Devops roadmap Playlist Hope you learnt something new from this .
